Chain of authority for public key certificates
Background
DigiStamp publishes the public key for each of its timestamp servers. The public key is used to verify the authenticity of the timestamps that you have created using the DigiStamp service.
Each DigiStamp server goes through an external audit process. This process creates an Audit Certificate within the secure hardware. The purpose of the design is to ensure that each timestamp key-pair is created within the audited hardware. This method ensures the private key is never revealed and that the clock cannot be tampered with. This Audit Certificate is the parent of each of the subsequent timestamp certificates. The child timestamp certificate key-pairs are replaced frequently within the hardware device; the Audit Certificate is never changed during the life of the server. The parent-child relationships are maintained by standard x.509 certificate chaining methods.
Each audited hardware device will have a unique Server Audit Certificate. These Audit Certificates are issued by a single DigiStamp internal self-signed CA. "Self-signed" means that the chain of authority does not continue beyond this certificate; described as a root certificate. Click here for an image of this hierarchy.
Does your company have an "internal CA" Certificate Authority
All of the DigiStamp public keys are provided in the form of x.509 certificates. You can choose to put the DigiStamp public key in a different x.509 certificate that you create. This would be done when you want to replace the DigiStamp Root CA. For example, you would do this if your organization has an internal PKI CA authority. The result is that your PKI CA becomes the Issuer of the public key certificate. To facilitate this process, DigiStamp provides the public keys in standard PKCS #10 certificate request that you can download below. Using this process, you can create a chain of authority as shown in the diagram below - there are two alternative approaches.
Using your PKI, you can replace the certificates that are highlighted in red below.
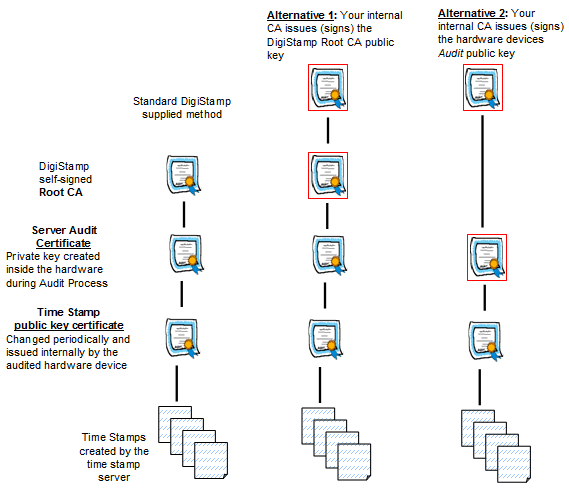
Alternative 1: This approach replaces only the DigiStamp Root CA. Your internal CA becomes the issuer of this public key. This means that DigiStamp can sign the Audit Certificates of many time stamp servers and all of those Audit Certificates (child certificates) would be trusted.
Alternative 2: This approach replaces the individual Server Audit Certificates. The replacement certificate would be rooted in your internal CA. This means that you have designated that you trust a specific DigiStamp server. This alternative is practical when you have exclusive use of one of our servers or you purchase our SecureTime Server.
The Certificate Requests are downloaded as DER encode PKCS #10 records. Certificate chaining uses the x.509 data element Subject Key Identifier, or called "Local Key ID" in the PKCS #10 request.
|
|
CSR - Certificate Signing Request
|
ECC-NIST |
ECC-Brainpool |
RSA |
|
|
Root CA |
p10 csr |
p10 csr |
p10 csr |
|
|
Robot TSA 1 - Audit Certificate |
p10 |
p10 |
p10 |
|
|
Robot TSA 2 - Audit Certificate |
p10 |
p10 |
p10 |
|
|
Robot TSA 3 - Audit Certificate |
p10 |
p10 |
p10 |
