Archive using Hash-Linking for PKI renewals
Generally, if you are protecting data for 5 to 10 years then the risk of technology obsolescence is low and therefore our Archive does not add value for you. Except, the feature that if you loose your digital timestamp we still have a copy (you will need to keep the original, timestamped file).
Why an Archive?
Answer: Longevity of your document’s e-TimeStamp proof
The Archive enables document archiving for 25+ years; and potentially further, we use the industry standard methods that were designed for continual maintenace of provable data integrity.
Use Case
Scenario: 7 years from now it becomes important to be prove the authenticity of a timestamped PDF document. But, there has been a problem: in that 7-year period a problem was discovered that compromised the RSA 2048 algorithm (for example, due to advances in quantum computing). In this case, DigiStamp can provide you additional proof of your timestamps validity. That proof is a “renewal” timestamp. Your PDF file would still be provable as existing and authentic from the original timestamp time even though the original timestamp RSA 2048 had become compromised.
The renewal requires no action on your part, DigiStamp does this renewal for all the timestamps we created.
Summary Technical Explanation
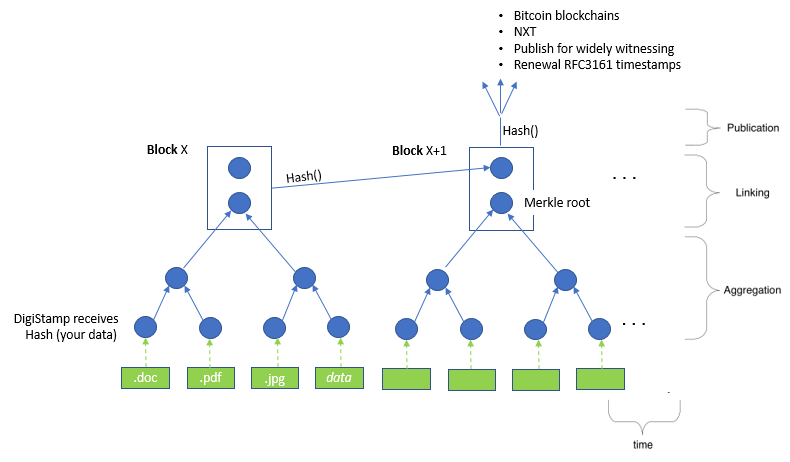
Each e-TimeStamp is placed in sequence with the others on the Archive Server. At the increment of the External Review time, a Merkle tree is built that starts with the root hash of the previous External Review's Merkle tree and contains all the timestamps created since the previous External Review Time. This new root hash is then published and protected through multiple mechanisms.
A Merkle tree is constructed with the individual timestamps. DigiStamp's Archive is a series of these Merkle trees over time.
Long term Archiving of digital data is a difficult problem and the solution was not designed by DigiStamp, we implement the service. The engineering for processing and syntax was defined by the IETF in RFC 6283 “Extensible Markup Language Evidence Record Syntax”.
The methods include, in combination:
-
Timestamp signature Renewal Allows for future enhancements in key lengths and algorithms. Soon, the archive will incorporate signatures with new, superior, public key cryptography.
-
Hash-chaining A hash-chain uses no secret keys, instead relying solely on cryptographic hashes like SHA2. The hash-chain links each timestamp request to those that came before it with keyless signatures. This structure is maintained as a long Merkle forest containing individual trees that have been chained together, continously renewed as new trees are appended.
-
Widely witnessed time stamping The hash-chain is then protected by securing its root hash with additional DigiStamp timestamps from all 3 of our active SecureTime TSAs using RSA 4096 and ECC 5xx, and by being published on our website.
-
Public blockchain entries The hash-chain root hash is also recorded into the distributed blockchain technology platforms of Bitcoin and NXT as add-ons to widely witessed method. However, most of that value is in the future if/when/how the blockchain is widely accepted. There is risk that these distributed ledgers will not be maintained in the long-term and we use them only as non-critical supplements.
-
The DigiStamp Archive will ensure that the timestamps we provide to you can be reliably verified for many decades to come, and in most cases with no additional action by you. All of this protection is in addition to the superior strength of the DigiStamp e-TimeStamp.
Brief social and technical history
Most business documents have a short lifespan - for examle, 7 years from now your tax receipts are likely not very important. However, some records require greater longevity.
Consider that print is dead, and with it some intrinsic integrity features. Digital forgeries are substantially easier to create than physical ones. We risk losing confidence in the aunthenticity and integrity of records if we do not utilize reliable methods to verify them.
Falsification of historical records is a social issue and requires social infrastructure. "He who controls the past controls the present and he who controls the present controls the future", George Orwell.
Social infrastructure in our age includes IETF - the IETF organizes technologists with the primary motivation of designing good solutions and openly publishing the details for use or criticism by the public. This process continues to produce foundational standards for global technology infrastructure.
For 15 years DigiStamp has operated a cloud based IETF RFC 3161 PKI timestamping service. In 2014 DigiStamp added the natural follow on:
Hash Chaining and a Timestamp Archive with Renewal as defined in IETF RFC 6283 Evidence Records for Long Term Archiving
The underlying methods are also associated with ISO-18014-3 ISO/IEC JTC 1/SC 27, "Time stamping services - Part 3: Mechanisms producing linked tokens"
How is a technology / timestamp renewal performed?
In the future, if failure of the Digital Signing algorithm (RSA or ECC) is feared, a timestamp can be renewed by creating a record of its authenticity (a timestamp of the timestamp) using improved signing technologies. Timestamping will demonstrate that the signature in the original timestamp was valid before the signing algorithm failed, and thus it will continue to be valid.
If the failure of a Hashing algorithm is feared, the still unaltered data must be hashed with a more secure Hashing algorithm and combined with the prior timestamp to create a new time stamp. DigiStamp will not be able to execute this process without the involvement of a Relying Party that has possession of the original, unaltered data.
Technical Details about XML Evidence Records
The definitive guides are the IETF standards documents.We are grateful for the IETF’s engineers for reviewing, debating and ultimately clarifying methods and protocols. Additional links outside the IETF that we thought would be helpful: Long-Term Archiving and Notary Service Evidence Record Syntax.
Warranty
DigiStamp Public Policy commits us to maintains our Archive and execute additional renewals as need to preserve the timestamp quality of evidence related to cryptic obsolescence.
The DigiStamp warranty is: If a timestamp’s original crypto method is compromised within 7 years of creation then you have free access to DigiStamp's Archived renewals for that timestamp. After that 7 year period you would need to purchase Archive Access from DigiStamp. Timestamps created since January 2016 are included with this warranty. This wording of this warranty is still in draft form and will not be finalized.
If a timestamp’s original crypto method is compromised within 7 years of creation then you have free access to DigiStamp's Archived renewals for that timestamp.
Understanding Cryptology FALLBACK failure risk of "missed renewal": the IETF standards intent that a renewal is performed if 1. the public key algorithm of the timestamp or 2. the hash algorithm used to build a Merkle tree is going to become insecure. This renewal must be done "before algorithm becomes insecure". There could be unforseen reasons why DigiStamp would be unable to perform the renewal whereby your timestamp authenticity would be lost. Alternatively, you can perform your own timestamp renewal action (these are published IETF procedures described in XML Evidence Records section above).
The other failure risk with no Cryptology FALLBACK: the hash algorithm used to hash your original data becomes insecure. We have added support for SHA3 hash-algorithms to help with this risk. To perform this renewal, your original data is needed, and DigiStamp does not have that file. The solution, and we will help you, is a renewal whereby you need to create a new timestamp request with an upgraded hash value of your original document. As background: All of these timestamp renewal methods are part of IETF published methods related to the basic problem of long term archive of digital data. Any of these renewal can be done without involving DigiStamp, they are public domain, accepted techniques described in technical standards.
