Repository of Timestamp Public Key Certificates
Contents
- Root certificate and how public keys are organized
- What does all this mean?: ECC, NIST, RSA
- Web addresses / URL for timestamp servers
- Test / Evaluation TSA public key certificates
Current CA and Issuer public keys
These CA certificates would be download just one time as part of your system setup. Then, these certificates are used to verify the secure issuance of the individual Time Stamp certificates that are delivered with each timestamp transaction.
| ECC-NIST | ECC-Brainpool | RSA | ||
| DigiStamp Root CA Certificate | certificate | certificate | certificate | |
Certificate's SHA-1 |
605c4f9c4a28e0284b12 3ae2b35be7e1cbe77f7b |
4b8c0d101f521648b148 4becac7a8f9f86d47ce0 |
b17c8dfb0ce68c5e89d1 9c062dc5668e081d456d |
|
|
Robots - Audit Certificates |
||||
TSA 1 |
certificate | certificate | certificate | |
TSA 2 |
certificate | certificate | certificate | |
TSA 3 |
certificate | certificate | certificate | |
Root CA and all Audit |
bundled in PEM | bundled in PEM | bundled in PEM | bundle all algorithms |
|
Curent Timestamp certificates these are changed about every 6 mos. |
||||
TSA 1 . Timestamp Common |
certificate | certificate | certificate | |
TSA 2 . Timestamp Common |
certificate | certificate | certificate | |
TSA 1 . Timestamp Long |
certificate | certificate | certificate | |
TSA 2 . Timestamp Long |
certificate | certificate | certificate |
Many individual Time Stamp certificate.
What are the Certificate?
The public keys are provided for independent verification of the timestamps created by the DigiStamp timestamp servers. Each public key is provided as a standard x.509 certificate. The public keys are used to verify the digital signature contained in a timestamp. These certificates are commonly contained within each timestamp and they are also provided here for convenience.
Click here for additional information about what you need to verify a timestamp. .
DigiStamp Root CA Certificate
The root certificate can be downloaded and added to your software. For example, Adobe Acrobat signing tools.
What does all this mean?: ECC, NIST, RSA
We suggest you use of ECC-NIST, but you have choices. These are 3 different encryption algorithms, you can choose which one is used to create your timestamps.
Details:
- NIST is the US National Institute of Standards and Technology.
-
ECC is the abbreviation for Elliptic Curve Cryptography.
The choice is between the RSA or two elliptic curve options of ECC-NIST (NIST Recommended) or ECC-BP (Brainpool) is nebulous; "USA" versus "EU" preference is "USA" compared to "EU" preference is one perspective. The NIST curves currently have wider acceptance; for example, Brainpool is not currently supported in Adobe products, but it is in Microsoft products. Your DigiStamp account setting was setup to use ECC-NIST and if choose otherwise then you need to make a change to that setting to your account click here, at the bottom of the page see "timestamp type".
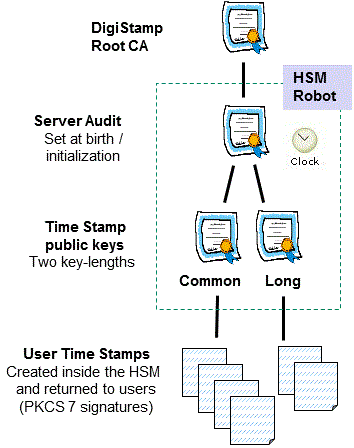
Timestamp key life cycle
The timestamp key-pairs are replaced frequently within the certified hardware device. The frequency is one year or after one million timestamps are created with the key-pair. Each event of "rekeying of the TSA key" results in the cryptographic module creating and signing a new x.509 public key certificate. The previous timestamp private key is destroyed at the time of rekeying. The timestamps created with that private key are authenticated using the x.509 public key certificate. More details are here where we describe that the timestamp private key cannot be extracted from the certified hardware device.
Name and addresses of the Timestamp Server
The time stamp servers are available to generate production time stamps:
Best choice, find a location for me:
https://tsa.digistamp.com at IP address 23.253.108.54
Or, use specific servers. Possibly in a failover or Round Robin configuration:
"TSA1" -https://tsa1.digistamp.com at IP address 38.135.35.138
"TSA2" - https://tsa2.digistamp.com at IP address 68.70.162.26
The above servers use HTTP authentication using your DigiStamp account credentials. Use of SSL (https:) is optional.
Optional, IP Address Based Authentication
Background: When you connect to the Internet (for example, at home or in the airport) you get a unique IP address assigned to your computer. You can configure your DigiStamp account to accept timestamp requests from that IP address. This means that DigiStamp gives timestamps without checking your account password, if that request comes from that IP address. More from wikipedia about your Internet Global IP address that is used to authorize your timestamps requests.
If you are using this IP-Based Authentication (instead of the typical HTTP authentication) then login to your DigiStamp account and enable DigiStamp's IP-based Authentication option here, scroll toward the bottom of the page. Your IP address will change with different Internet connections, so you may need to return to your account settings to update this value. Then the Timestamp Server names given above are changed like this:
append "/ipauth" to the URL
Example:
https://tsa.digistamp.com/ipauth or for "TSA1" -https://tsa1.digistamp.com/ipauth
